The Threat of DDoS Attacks on WordPress Sites
If your WordPress site suddenly slows to a crawl or goes offline, you could be facing a DDoS attack. These attacks aren’t limited to high-profile brands. Blogs, eCommerce stores, and digital agencies are common targets and the impact can be immediate and costly.
A DDoS (Distributed Denial of Service) attack overwhelms your site with non-human traffic. Thousands of automated requests hit at once, draining server resources and locking out real users. It’s fast and difficult to trace, and no plugin or manual fix is enough to stop it. Without infrastructure-level protection to detect and deflect the surge, your site stays vulnerable.
So let’s explore how DDoS attacks work, what you can do to minimize risk, and why a secure hosting platform is essential for long-term resilience.
What DDoS Attacks Are & How They Work
A DDoS attack overwhelms your website by flooding it with fake traffic. These attacks are powered by botnets (networks of infected devices such as compromised computers, smartphones, and smart routers) all programmed to send repeated requests to your site. The resulting traffic surge can quickly overload your server, slow down performance, and eventually take the site offline.
On WordPress sites, DDoS attacks typically fall into two main categories:
Volume-Based Attacks
Volume-based attacks rely on brute force. Attackers use automated bots to send large volumes of junk traffic, consuming bandwidth and draining server resources.
A common tactic involves targeting high-traffic areas, such as the homepage or product listings, with millions of requests. In eCommerce scenarios, attackers often go after the checkout process or search function, disrupting the shopping experience for legitimate users.
Application-Layer Attacks
Application-layer attacks are more targeted and difficult to detect. Instead of overwhelming the entire site, attackers focus on specific WordPress features while imitating real user behavior.
One method involves sending thousands of fake login attempts to overload the authentication system. Another involves exploiting xmlrpc.php, a WordPress file used for remote publishing and pingbacks, to silently generate a high volume of server requests. Because this traffic appears legitimate, it often goes unnoticed until performance issues emerge.
Why DDoS Attacks Are on the Rise
What makes DDoS so dangerous is how easy it is to launch. Attackers no longer need advanced skills or expensive tools. For just a few dollars, they can rent botnets or use DDoS-for-hire services available on underground marketplaces. These attacks are automated, low-cost, and built to overwhelm. As a result, they’re becoming more frequent and more disruptive, even for smaller WordPress sites.
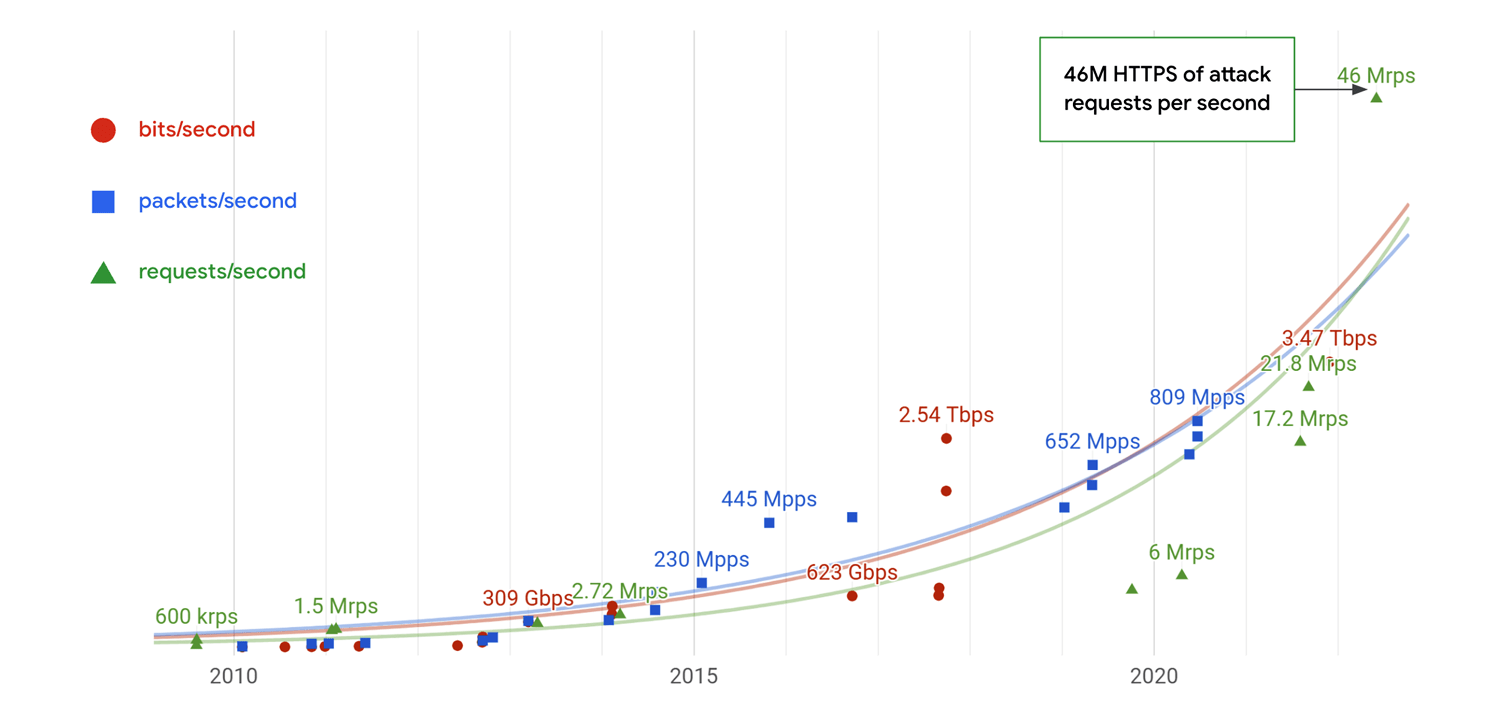
According to Google’s global threat analysis, the total number of DDoS attacks is rising each year and attackers are deploying more sophisticated, higher-volume methods.
Real-World Consequences of a DDoS Attack
The real damage of a DDoS attack goes beyond a temporary slowdown. It impacts revenue, trust, and performance across your entire digital ecosystem. Even a short disruption can have ripple effects that last far longer than the attack itself.
Here’s what’s at stake:
- Website Downtime. Visitors see error messages like 503 Service Unavailable, which drives them away instantly.
- Lost Revenue. If you run an eCommerce store, even a few minutes of downtime during a peak period can mean thousands in lost sales.
- SEO Damage. Google may lower your search rankings if your site becomes unresponsive or has a high bounce rate.
- Bandwidth Overage Charges. Hosts that charge based on usage may bill you for all the junk traffic hitting your site.
- Server Crashes: Persistent high traffic can overload memory and CPU, potentially taking your whole server offline.
- Reputation Loss: Users, customers, or clients may lose confidence in your brand if your site is unstable or unreliable.
What You Can Do to Defend Your WordPress Site
While you can’t stop all DDoS attacks on your own, there are smart actions you can take to reduce your exposure and improve your site’s resilience. These are client-side measures, tools, and tactics you can control directly as a WordPress admin or developer.
1. Limit Access to wp-login.php
The WordPress login page is one of the most common DDoS targets. Here’s how to lock it down:
- Use two-factor authentication. This adds an extra layer of security beyond just a password, making it harder for bots to break in.
- Enable reCAPTCHA. This protects from automated login attempts by requiring users to verify they’re human.
- Limit login attempts with a plugin like Limit Login Attempts Reloaded. This stops brute-force attacks by locking out IPs after a set number of failed tries.
- Consider changing the login URL with a plugin like WPS Hide Login. Obscuring your login page makes it harder for bots to find and target it in the first place.
- Block (or allow) access to
wp-login.phpby IP using.htaccessor server rules. Access your website files via SFTP and add this to your site’s root.htaccessfile (where WordPress is installed):
<Files wp-login.php>
Order Deny,Allow
Deny from all
Allow from xxx.xxx.xxx.xxx
</Files>Replace xxx.xxx.xxx.xxx with your IP address. You can add multiple Allow from lines if needed for additional users or admins.
Don’t forget to whitelist your current IP or you’ll get locked out.
2. Disable Unused Features
If you’re not using certain WordPress features, turn them off to reduce your attack surface. Here are some quick wins:
→ Disable xmlrpc.php
The xmlrpc.php file is a legacy feature in WordPress that allows remote connections, like publishing blog posts from a mobile app or connecting to Jetpack.
If you’re not using those kinds of integrations, it’s best to disable it. This file is a known target in DDoS and brute-force attacks because it can be used to send a flood of requests to your server.
You can disable this file by using a plugin like Disable XML-RPC or via the .htaccess file by adding the following code:
<Files xmlrpc.php>
Order Deny,Allow
Deny from all
</Files>Make sure you back up .htaccess before making changes.
→ Disable pingbacks and trackbacks
Pingbacks and trackbacks are WordPress features that notify you when other blogs link to your content. While they were once useful, today they’re rarely needed and often exploited in spam and DDoS attacks.
To disable them, navigate to ‘Settings → Discussion’ in your WordPress dashboard.
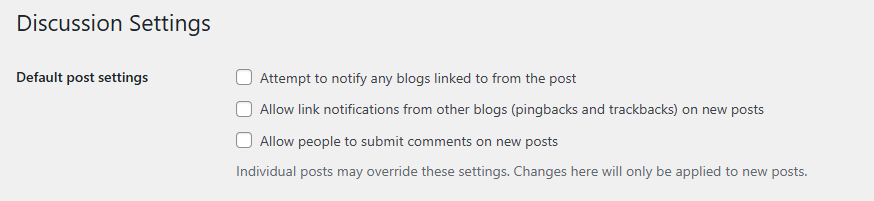
Make sure “Allow link notifications from other blogs” is unchecked and save the changes.
The WordPress REST API lets other applications communicate with your website. It’s what plugins, apps, and services use to fetch or update data behind the scenes.
While it’s useful, it can also expose sensitive information if not properly secured. That’s why it’s a good idea to restrict access for users who aren’t logged in.
- Use a Plugin. Install and activate the Disable REST API plugin to restrict REST API access for non-logged-in users.
- Manually via Code Snippet. If you’re comfortable editing your theme files, you can paste this into your
functions.phpfile to block unauthorized API requests:
add_filter('rest_authentication_errors', function($result) {
if (!is_user_logged_in()) {
return new WP_Error('rest_not_logged_in', __('You are not currently logged in.'), array('status' => 401));
}
return $result;
});A quick heads-up: editing theme files directly can break your site if something goes wrong. Always back up your site first, and use a child theme if you’re modifying code.
→ Remove unused themes and plugins to minimize potential entry points.
Inactive themes and plugins can still pose security risks if vulnerabilities are present. Go to ‘Appearance → Themes’ and delete any unused themes. Then navigate to ‘Plugins’, deactivate, and delete any plugins that are not in use.
3. Keep Everything Updated
Outdated WordPress core, plugins, and themes create security risks. Keep everything updated regularly to patch known vulnerabilities.
Enable auto-updates for trusted items to simplify maintenance. Use a staging site, if possible, to safely test major updates before going live, and always create a backup before making changes.
Staying current is one of the easiest and most effective ways to secure your site.
4. Use a Security Plugin
Security plugins won’t stop a DDoS flood, but they can help log events, alert you to anomalies, and harden your site against smaller attacks. Use a well-supported plugin like Wordfence Login Security or Sucuri Security.

Wordfence Login Security is a lightweight plugin focused on securing the login process. It adds 2FA for admins and users, includes reCAPTCHA, and blocks login attempts via XML-RPC.
Sucuri Security is a broader security suite focused on site integrity and alerting. It monitors file changes and unauthorized modifications and logs user actions, failed logins, and file upload attempts. Moreover, you can use it to send alerts for blacklisting or abnormal behavior.
We recommend using one security plugin to avoid conflicts and keep your site performant. Choose depending on our needs as always.
5. Monitor Traffic for Spikes and Anomalies
Here are some helpful tools to monitor your site and catch unusual traffic early
Tools you can use now:
- UptimeRobot or Better Stack gets alerts if your site goes down or takes too long to respond.
- Cloudflare analytics is a free, privacy-focused way to track visitor data and spot traffic spikes.
- New Relic and Query Monitor are ideal for advanced users. These tools help you track performance bottlenecks, database activity, and server behavior. Best used with premium hosting environments.
- Server logs and access logs, if available in your hosting panel, help review traffic patterns manually to spot anything unusual.
These tools are a great starting point and they’ll absolutely help you catch early signs of trouble. But it’s important to know that no plugin or DIY fix can handle a large-scale DDoS attack on its own.
That’s where your hosting provider comes in. Let’s take a look at how a secure host can keep your site protected at the infrastructure level.
What Hosting Providers Should Do (Server-Level DDoS Defense)
Your hosting provider plays the biggest role in determining whether your site stays online during a DDoS attack or collapses under the load. Here’s what a reliable host should provide:
Enterprise-Grade Network-Level Protection
The host should operate behind DDoS-mitigated upstream providers and use advanced traffic filtering at the network edge. That means malicious traffic gets blocked before it even touches your WordPress environment.
Look for:
- Built-in protection against volumetric and application-layer attacks
- Automatic rate-limiting and traffic-filtering policies
Infrastructure That Can Absorb Spikes
Even with filtering, large attacks generate high load. A secure host needs:
- Load-balanced architecture to distribute traffic
- Auto-scaling or burst-handling capacity
- Isolation between accounts so one site doesn’t affect other websites on shared infrastructure
24/7 Monitoring and Response
DDoS attacks often happen outside business hours. A solid host should have real-time monitoring and human engineers available 24/7 to respond.
They should be able to detect attacks within seconds, apply emergency mitigation rules and communicate status transparently to affected clients
Configurable Access Controls and IP Filtering
You shouldn’t be stuck with just plugin-level controls. Your host should give you the tools to block (or whitelist) IPs and restrict sensitive endpoints like wp-login.php and xmlrpc.php at the server level.
Unless your hosting provider delivers on these essentials, your site remains vulnerable. True DDoS resilience starts at the infrastructure level, where real protection happens.
That’s exactly where Pressidium stands apart. Let’s take a closer look at how our platform is built to neutralize DDoS threats before they impact your WordPress site.
How Pressidium Protects WordPress Sites from DDoS Attacks
At Pressidium, DDoS protection isn’t an afterthought. It’s engineered into the core of our platform. Every layer of our platform, from the edge network to the app, is built to identify and stop attacks before they impact your site.
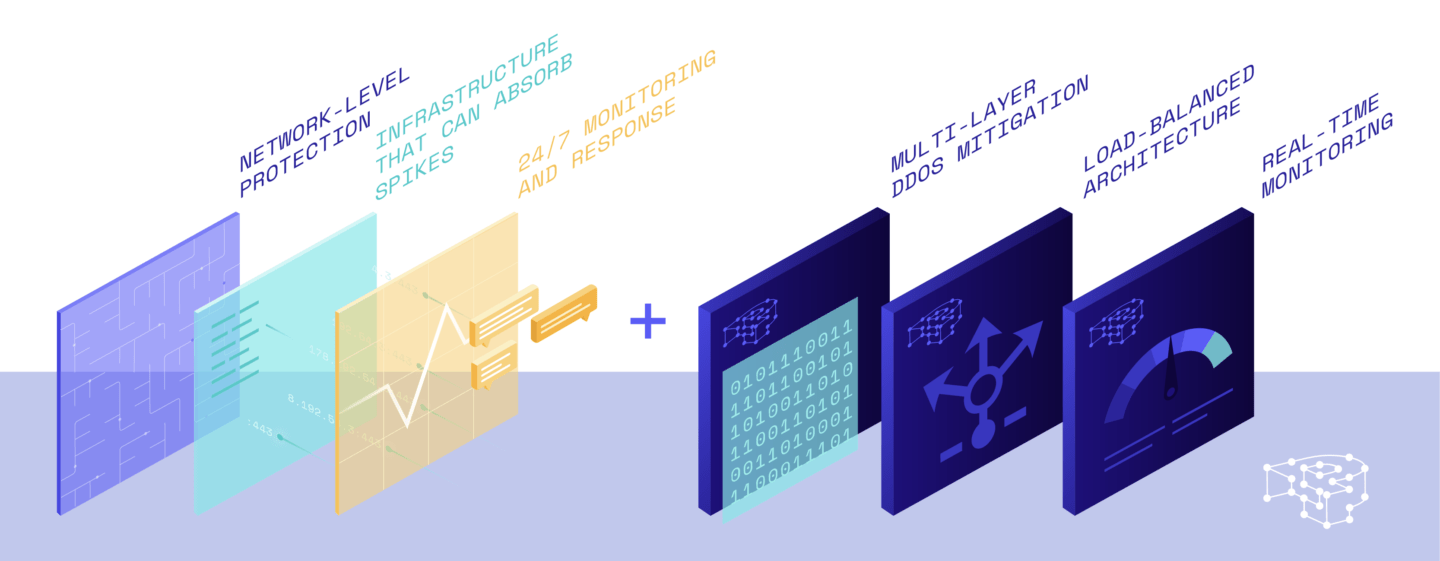
Here’s what we deliver for DDoS protection across every plan, without exceptions:
Multi-Layer DDoS Mitigation, Built-in
Our platform operates behind multiple upstream providers with DDoS mitigation at the network edge. Malicious traffic is stopped at the edge, reducing load on your WordPress environment, and minimizing the chance of overload.
- Intelligent rate limiting. We automatically slow down or block traffic that exceeds normal usage patterns, helping prevent resource exhaustion from sudden traffic spikes.
- Protocol filtering. Our system inspects traffic based on the communication protocol used (like HTTP, DNS, or TCP) and blocks anything suspicious, including low-level attacks like SYN floods or ICMP floods.
- Geo-based traffic control. We can detect and control traffic from specific countries or regions, helpful for stopping botnet activity originating from known hotspots.
- Comprehensive protection. Covers both volumetric and application-layer attacks, ensuring your site stays accessible and stable.
There’s no need to install or configure anything. We handle it all automatically.
Load-Balanced Architecture with High Availability
Pressidium’s environment uses a load-balanced infrastructure that automatically distributes traffic across multiple nodes. During an attack, your site remains stable because it’s not tied to a single point of failure.
Our platform is designed to absorb traffic spikes while maintaining consistent performance for legitimate users.
Real-Time Monitoring and Proactive Response
We don’t wait for problems to escalate. Our automated systems and DevOps engineers continuously monitor for unusual traffic patterns and act immediately to contain threats.
- 24/7 platform monitoring by expert engineers
- Instant deployment of mitigation rules
- Transparent incident reporting and client communication
Application-Specific Hardening for WordPress
Because we specialize in WordPress, our platform is tuned to protect the areas most commonly targeted in DDoS and bot attacks.
- Login and XML-RPC protection. Key files like
wp-login.phpandxmlrpc.phpare automatically hardened and continuously monitored. - Smart rate limiting. We detect unusual traffic patterns and apply rate limits at the platform level keeping things fast for real users while blocking abuse.
- Targeted request filtering. Abusive requests are isolated and neutralized without affecting legitimate visitors or disrupting your site’s performance.
No Surprise Costs or Overages
You won’t get charged extra just because someone tried to flood your site with junk traffic. We don’t penalize you for being attacked, no hidden bandwidth fees, no unexpected bills.
Stay Online. Stay Protected.
DDoS attacks are evolving. So is our platform. Pressidium doesn’t rely on reactive tools nor push responsibility back to the user. We provide proactive, infrastructure-level protection from the ground up so your site stays fast, secure, and online.
You can’t predict when a DDoS attack will strike. But you can choose a Managed WordPress Hosting provider that’s ready for it.
Start your free trial today and experience the difference.
Start Your 14 Day Free Trial
Try our award winning WordPress Hosting!