Why You Should Take Brute-Force Attacks Seriously
Brute-force attacks are one of the most persistent cybersecurity threats to WordPress websites. They don’t just threaten security, they disrupt business operations. A successful attack can compromise user accounts, inject malware, or deface a site. Even unsuccessful attempts may degrade site performance, increase hosting costs, and erode customer trust. For businesses, the stakes are even higher: lost revenue, downtime, and reputational damage.
Brute-force attacks are relentless, but they’re not unstoppable. With the right security measures, you can dramatically reduce the risk. This guide breaks down how these attacks work, their impact on WordPress sites, and the best ways to defend against them.
Before diving into protective measures, it’s essential to understand how brute-force attacks operate. By recognizing their methods, you can build stronger defenses.
How Brute-Force Attacks Work
Brute-force attacks rely on automation, allowing hackers to test thousands, even millions, of username-password combinations until they find a match. While this method may seem unsophisticated, it remains highly effective against weak credentials.
These attacks come in different forms, each varying in complexity and effectiveness. Here are the most common types:
1. Standard Brute-Force Attacks
Attackers systematically try different combinations of letters, numbers, and symbols. A basic sequence might look like this:
- password1
- password123
- Password!2024
- Admin2023!
With automated tools, they can test thousands of variations per second, quickly cycling through possibilities.
2. Dictionary Attacks
Instead of random combinations, dictionary attacks use lists of common passwords. Some of the most frequently used passwords include:
- 123456
- qwerty
- letmein
- admin
- welcome2024
As long as weak passwords exist, dictionary attacks will remain a highly effective attack method.
3. Credential Stuffing
This method takes advantage of previously leaked username-password pairs from past breaches. If a user reuses the same password across multiple sites, attackers don’t even have to guess – it’s already in their database.
For example, if a user’s login details (john@example.com / password123) were exposed in a breach, hackers will test those credentials on other platforms, including WordPress sites, hoping for a match.
Do not confuse dictionary attacks with credential stuffing. Dictionary attacks use common guess passwords for a single account, while credential stuffing exploits stolen username-password pairs across multiple platforms.
Understanding brute-force attack techniques is critical, but it’s equally important to grasp the serious consequences these attacks can have on your business.
The Impact of Brute-Force Attacks
Brute-force attacks can damage your website beyond just compromised passwords. From disrupted operations to severe financial losses, their impact runs deep.
A successful brute-force attack grants attackers full control over your WordPress site. Once inside, they can:
- Steal sensitive data. Customer information, payment details, and login credentials become exposed.
- Modify user permissions. Hackers can escalate privileges, locking out legitimate admins.
- Embed malicious scripts or install malware, often undetected, to steal data or infect visitors’ devices.
- Deface your website. They replace content with spam, political messages, or phishing pages.
- Turn your site into a botnet node. Attackers hijack your server to spread malware or participate in larger cyberattacks.
Beyond operational damage, these breaches also trigger financial and legal consequences. Companies face regulatory fines, lawsuits, and reputation loss, which can take years to recover from.
Lockouts and Service Disruptions
Repeated brute-force attempts often trigger automated security defenses, locking out users, including legitimate administrators and customers. These lockouts disrupt internal operations, preventing essential administrative tasks like content updates, sales monitoring, or customer support activities.
For customers, lockouts cause frustration and erode trust, potentially pushing them toward competitors. Extended or frequent disruptions further damage your site’s reliability, negatively affecting customer experience and long-term loyalty.
Performance Degradation and Server Overload
Brute-force attacks, even when unsuccessful, put a heavy strain on your server. Constant login attempts consume CPU and memory, slowing down your site. If the attack continues, it can overload the database, crash the server, and drive users away.
Reputational Damage and SEO Impact
Security breaches severely undermine customer trust. When visitors encounter a hacked website, they lose confidence rapidly and may never return. Additionally, search engines may blacklist or lower rankings for hacked sites, reducing organic traffic and visibility. Moreover, regaining customer trust and SEO rankings after a security breach is slow and costly.
Financial Consequences
The costs of mitigating a brute-force attack go beyond immediate recovery. Businesses may need to invest in forensic analysis, malware removal, and security upgrades. Downtime leads to lost revenue, especially for eCommerce sites that rely on uninterrupted transactions. For businesses handling customer data, regulatory fines (e.g., GDPR, CCPA) may apply, increasing recovery costs.
How to Defend Against Brute-Force Attacks
Given these serious impacts, proactively securing your WordPress site against brute-force attacks is crucial. Here’s how to strengthen your defenses effectively.

1. Use Strong, Unique Passwords and Enforce Secure Authentication
Weak passwords are a primary target in brute-force attacks. To prevent easy breaches:
- Require passwords that are at least 16 characters long, with a mix of letters, numbers, and symbols.
- Avoid predictable patterns like
password123, names, birthdays, or dictionary words. - Implement a password policy manager plugin to enforce strong passwords across all user accounts.
- Use a password manager (e.g., 1Password, Bitwarden, LastPass) to generate and store passwords securely.
- Introduce passwordless authentication to eliminate password-based vulnerabilities.
2. Enable Two-Factor Authentication(2FA) and Monitor Logins
Even strong passwords can be compromised. Two-factor authentication (2FA) adds an extra layer of security:
- Use an authenticator app like Google Authenticator, Authy, or Microsoft Authenticator instead of SMS-based 2FA, which can be vulnerable to SIM-swapping.
- Install a WordPress 2FA plugin like Two-Factor or WP 2FA. Require 2FA for admin accounts and encourage its use for all users with high privileges.
- Monitor failed login attempts and unusual activity using WP Security Audit Log or Sucuri Security.
- Require 2FA for admin accounts and encourage its use for all users with high privileges.
3. Limit Login Attempts and Block Automated Bots
By default, WordPress allows unlimited login attempts, making brute-force attacks easier. Reduce attack success rates by:
- Setting up temporary lockouts for repeated failed attempts and applying progressive delays to slow down attackers.
- Installing Limit Login Attempts Reloaded or Really Simple Security to restrict failed login attempts.
- Implementing CAPTCHAs and honeypots with plugins like Advanced Google reCAPTCHA to block bot-driven login attempts.
4. Keep WordPress Updated
Outdated software is a key security risk:
- Enable automatic updates for WordPress core, themes, and plugins.
- Remove unused or outdated plugins and themes to minimize attack vectors.
5. Change the Default Login URL and Restrict Access
Attackers often target wp-admin or wp-login.php. Strengthen login security by:
- Using WPS Hide Login to create a custom, non-guessable login URL.
- Restricting access to the login page by allowlisting specific IP addresses.
- Setting up emergency access recovery via SFTP or database changes in case of a lockout.
6. Regular Backups
Despite strong defenses, no system is foolproof. Backups ensure recovery after an attack:
- Use backup solutions like UpdraftPlus or VaultPress.
- Store backups off-site in cloud storage like Amazon S3, Google Drive.
- Regularly test backup restoration to ensure reliability.
Does Your Hosting Provider Protect Against Brute-Force Attacks? Here’s What to Check
While site-level protections are essential, your hosting provider plays a crucial role in security.
A well-equipped hosting provider strengthens your defenses through advanced security measures.
Machine Learning-Based Threat Detection
- Advanced hosting providers use machine learning to detect and block brute-force attack patterns in real time.
- Hosting security should analyze login behaviors and flag suspicious activity before an attack escalates.
Intelligent Rate Limiting and IP Reputation Monitoring
- Standard rate limiting only blocks repeated login attempts from a single IP.
- Advanced hosting security tracks login velocity, geo-location, and IP reputation databases to block attackers before they infiltrate your site.
Web Application Firewalls (WAFs) with Adaptive Security
- A high-quality hosting provider deploys a Web Application Firewall (WAF) to analyze login requests and block brute-force bots.
- Look for a WAF that updates dynamically based on new attack patterns, rather than relying on static rules.
Automated Login Activity Monitoring & Alerts
- Secure hosting should provide real-time login monitoring with automated alerts for failed logins and login attempts from suspicious locations.
- Geo-blocking capabilities allow you to restrict logins from countries known for cyberattacks.
If your hosting provider doesn’t offer these protections, your site is exposed to brute-force attacks at the infrastructure level. That’s where Pressidium stands out.
How Pressidium Protects Against Brute-Force Attacks
Pressidium provides enterprise-grade security that stops brute-force attacks before they even reach your site.
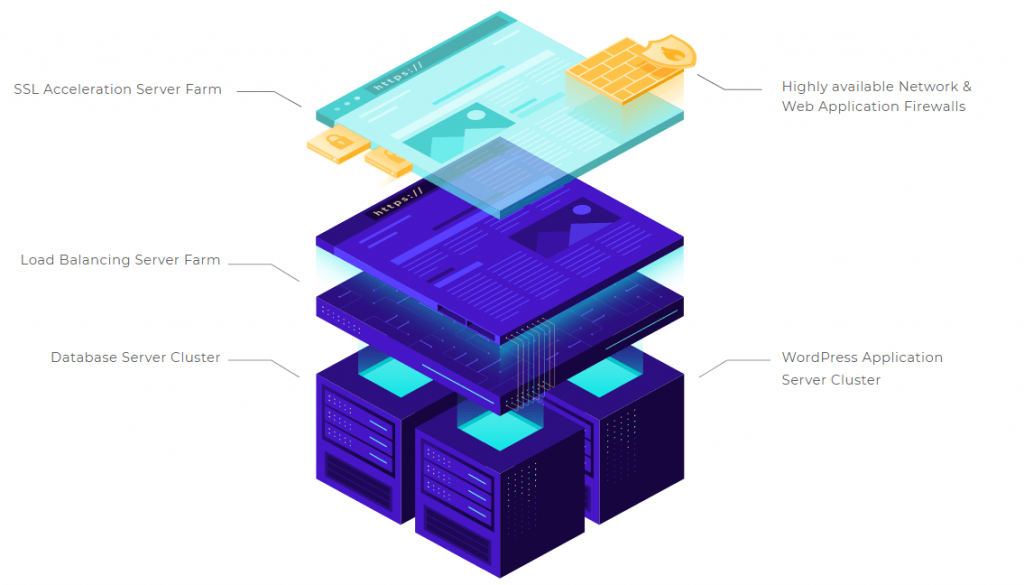
Proactive Brute-Force Protection
Pressidium’s Enterprise-Grade Web Application Firewall (WAF) and machine-learning-based security are built to stop brute-force attacks at the infrastructure level.
- Adaptive WAF analyzes login attempts in real time, filtering out bot-driven attacks before they flood your login page.
- Machine learning detects abnormal login behavior, preventing repeated failed attempts from overwhelming your server.
- Progressive IP blacklisting blocks attackers dynamically, rather than relying solely on static lists of known threats.
- Failed login attempts are analyzed for suspicious patterns, ensuring that real users are not mistakenly locked out.
Login Protection & Rate Limiting
Brute-force attacks involve high-volume automated login attempts, which can overload a site. Pressidium mitigates this at multiple levels:
- Platform-level rate limiting restricts the number of failed login attempts per user/IP to slow down bots.
- Adaptive throttling increases wait times dynamically, making repeated automated guessing attempts infeasible.
- Security at the platform level reduces reliance on additional security plugins.
- Encourages strong authentication, including strict password policies and 2FA for admin accounts.
Server-Level Attack Mitigation
Brute-force attacks can slow down or crash servers. Pressidium prevents this with infrastructure-based solutions.
- Traffic filtering isolates and blocks attack traffic before it reaches your WordPress login page.
- Server-level load balancing ensures uptime by distributing legitimate traffic efficiently.
- Unlike generic hosting, Pressidium adapts security in real time, rather than relying on outdated IP blacklists.
Automated Security Updates & Maintenance
Pressidium keeps your WordPress environment secure with proactive updates and patches.
- Critical security patches are applied automatically to prevent vulnerabilities from being exploited.
- Pre-tested updates ensure site stability, eliminating risks from unverified patches.
A Secure WordPress Hosting Environment
Pressidium’s proactive, infrastructure-level security neutralizes brute-force attacks at the server level, significantly reducing the need for additional security plugins or manual interventions.
We ensure high performance, uptime, and security, allowing WordPress site owners to focus on growing their business, not managing security threats.
Ready to experience secure, reliable, and worry-free WordPress hosting firsthand?
Start Your 14 Day Free Trial
Try our award winning WordPress Hosting!