Secure WordPress hosting is a term that is thrown around a lot these days. But what exactly does it mean? What does an enterprise hosting solution offer in terms of security, that regular hosting does not? We will delve into these questions and identify the design principles behind secure hosting environments. Armed with that information, you will be able to make an educated guess when researching hosting solutions for your business!
Regular hosting vs enterprise hosting security
Regular hosting is a bit like the Wild West. Your website gets hosted on a machine, running some version of a web panel software, allowing SSH connections, and then anything goes.
The hosting environment usually is not locked down, allowing a successful attacker to have access to all of the system’s files, including customer-related ones. This means that if an attacker gains access to a website that is hosted on the same server as your own, he or she has a very big chance of having access to your own files as well.
The security of a system is as strong as its weakest link. In a shared hosting environment, you are as secure as the least secure website hosted in that system.
What are secure hosting environments?
Modern secure hosting environments must observe the following design points:
- Filtering: traffic should be filtered for “abnormal” requests and remote attack signatures. Data should be sanitised.
- Fine-grained access control: Permissions and access controls should be layered, with no unnecessary extra privileges.
- Process isolation: A process (running an application or a system), cannot alter or modify the integrity of another.
- Do not trust anything the client sends you: treat all incoming requests suspiciously by default.
- Stripped-down, bare necessities environment: unnecessary installed software is usually a point of weakness. All the software installed in an environment should have a definite reason for being there.
Furthermore, in high availability n-tier architectures, the design for security is different. Each tier is provisioned separately, with different security mechanisms and policies in place. When an attacker takes control of a web server, he is prevented from gaining further access to the other tiers, for example, the database. In short: the compromising of one machine does not jeopardise the security of the whole system.
Pressidium’s Secure WordPress Hosting
We need not say much. We take security very seriously. Our Platform implements security mechanisms across many different layers. We put an effort in promoting the best WordPress security practices that exist today. Let’s see what’s under the hood!
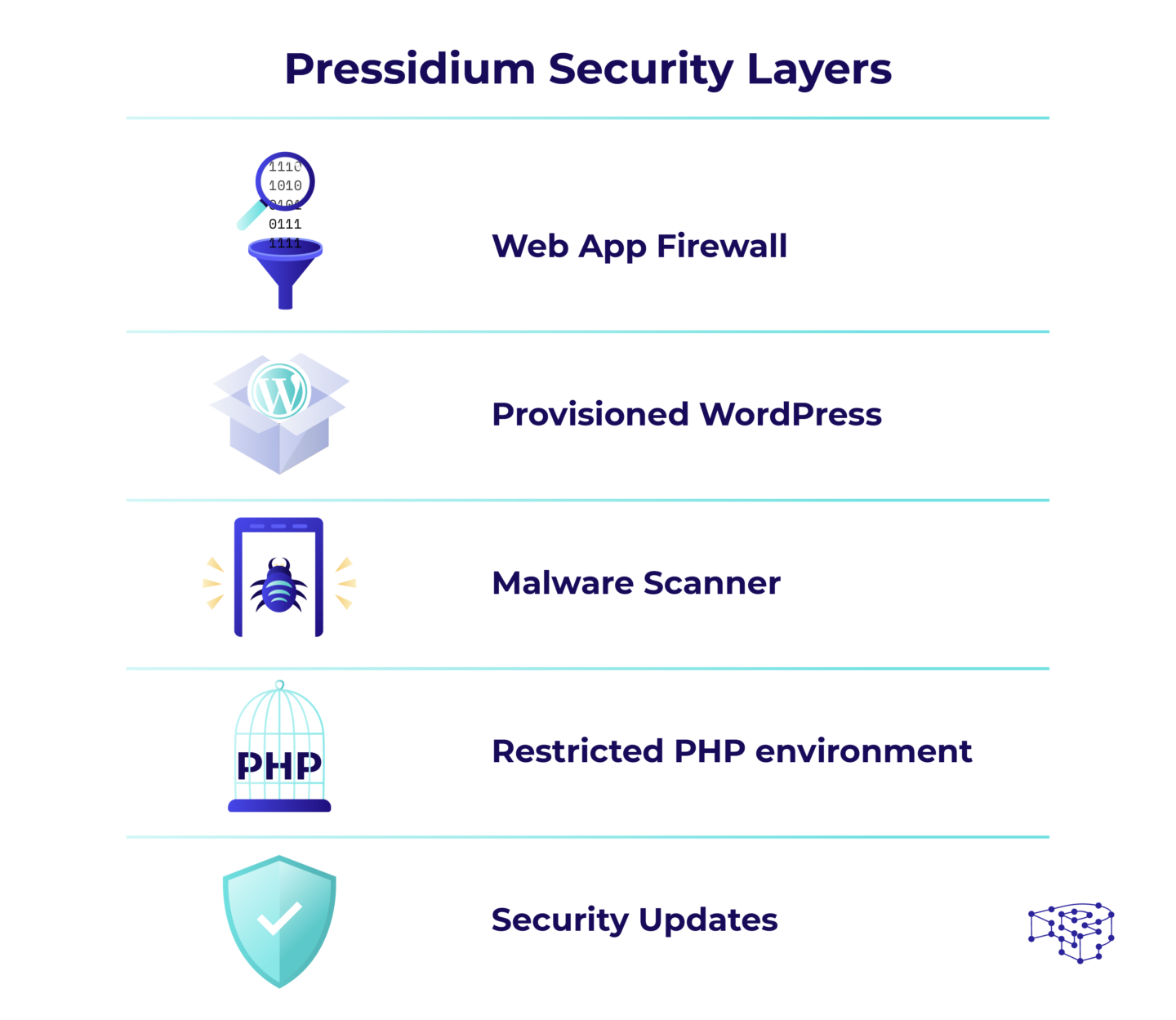
Restricted PHP
Our web servers run a locked-down version of PHP that can only execute WordPress related functions and nothing else.
Provisioned WordPress installation
The WordPress installation of your site cannot be modified (even by you) and is constantly sanity-checked by the Platform. The PHP compiler runs in user-space, under the chroot jail of a specific user. This means that even if a malicious attacker gains superuser access on a site, he or she will access only the files related to that site, and not yours, or the system’s.
Chrooted (jailed) environments
Everything that runs on our Platform is layered with different levels of restricted (chroot) environment. A chroot environment restricts the file system of a running process by modifying the place of the root directory. Nothing then can alter files outside of that root directory. Each process is in its own silo and cannot “see” or “touch” anything outside of that (this means your files too). Our Platform implements three different levels of chroot environments:
- per Site
- per User
- per Process
WordPress Update Layer
Our WordPress Security Updates ensure that you will always be up to date with the most stable version of WordPress there is. We update plugins and themes on a need for basis, and only if a security threat appears. We also do not update software at random, or without notice. Everything is coordinated with you personally.
Try our Award-Winning WordPress Hosting today!

Virtual Patching Layer
If you absolutely must keep old and outdated plugins, even if they are known to be vulnerable, you can use our virtual patching mechanism of our WAF Web application firewall. This mechanism intercepts attacks that are coming from known vulnerabilities. So plugins that are outdated and vulnerable, can continue to function as intended without posing security risks.
OWASP Filtering
Our Web Application Firewall is designed by following the Varnish Security Firewall model. Using OWASP rules and filters, the firewall prevents attackers from accessing your site’s weak points. Additionally, if an attacker initiates multiple connections as in a Denial Of Service attack, then the attacking IP will be throttled. Should any attack persist we enforce a block on a geographical level, even on whole countries when it is necessary.
Malware and Vulnerability scanning
We use resources like NIST’s National Vulnerability Database to scan every data we keep for malware, exploits and known security issues. We host a specific database that contains data signatures that help detect an incoming attack.
Brute-force attack ban
If an attacker tries repeatedly to test credentials, our Platform detects these attacks and bans the IP address on the firewall layer.
WordPress Security is our vision
We feel that WordPress security is important, and as it happens with most things that are important, it takes a serious effort to do it properly. That’s why we’ve built provisioning, sanity-checking, and filtering into the heart of our Platform. Our vision for a secure WordPress ecosystem is big, and we will share more details to the world in time. But for now, we need to pay attention to the little everyday things that make your WordPress business more robust, and less painful!
Start Your 14 Day Free Trial
Try our award winning WordPress Hosting!