Let’s Encrypt is an initiative that provides a free and automated way of securing the HTTP traffic of your website. Setting up secure HTTPS was always an involved process, and we’re happy to support any effort that makes the whole process simpler and more straightforward for people.
Generally speaking, in order to enable HTTPS on your website, you need to acquire a security certificate from a Certificate Authority (CA). A Certificate Authority is regarded as a trusted third-party that can verify a website’s identity to your visitors. The security certificate (also called SSL certificate) is installed on the web server and provides two functions: a) It encrypts all HTTP traffic between your website and your visitors b) It authenticates the identity of your website, so that your visitors know they are not visiting a bogus one.
Securing your website’s identity and visitor traffic is the obvious benefit here but there are also a few more that require further explanation.
Before Let’s Encrypt, you had to choose the type of certificate you wanted, a process that was a bit confusing to users not familiar with public key systems, then you had to generate your keys, sign a Certificate Generate Request and finally spend a considerable amount of money in order to purchase one.
Wait, but what is SSL?
The Secure Sockets Layer, or SSL is a cryptographic protocol that secures the communication of a network. It ensures the privacy of the communication, meaning that the data exchanged between two parties are encrypted and cannot be eavesdropped by a third party. It also authenticates the identity of the communicating parties, usually the server, by using the SSL certificate that we mentioned earlier.
How can you tell if a website is secure?
Websites that are secured by SSL are easily identifiable by a couple of things:
- There is a green padlock icon next to the URL address (depending on what browser you are using)
- The URL begins with https instead of http.
SSL certificates however also have an expiration date. When that date has passed, the communication is no longer secure, and the certificate needs to be renewed. You can easily check whether the SSL certificate of your website is expired or not by first clicking on the padlock icon and depending on what browser you use, do the following:
On Firefox, click the arrow button on the right, and then on the More information link. Finally click on the View Certificate button under the Security tab to view the certificate details.
If you use Chrome, click the Details link, and then the View certificate button under the Security Overview tab.
Under the Validity Period section, there are two dates related to the certificate. The Issued On and the Expires On. The first is the date that the certificate was activated, while the second is its expiration date. If the Expires On date has passed, the certificate needs renewal and the communication is no longer secure!
Why care about SSL?
Well, there are a number of reasons! Securing the communication between your website and your visitors, authenticating your website’s identity, ensuring data integrity between browser and web server, and even getting a higher SEO rank.
Secure communication and authenticated identity sound like nice things to have, but what are they protecting your website from ? The concept might seem nebulous to some. In reality those two work together in fighting perhaps one of the most classic attack methods documented in computer security. The “man-in-the-middle” attack (or abbreviated, MitM).
Try our Award-Winning WordPress Hosting today!

Let’s suppose we have a website operated by Alice, which is visited by Bob (the attack also works on different services, not just websites). So far so good. Then, there is this bad guy called Charles (bad guys in computer security are usually called Charles for some reason. Dry martinis and secret hideouts come to mind.)
Charles, by using a number of different techniques which are too complex to go into in this article, seizes the control of the communication channel between Alice and Bob. He sits quietly and invisibly, between them.
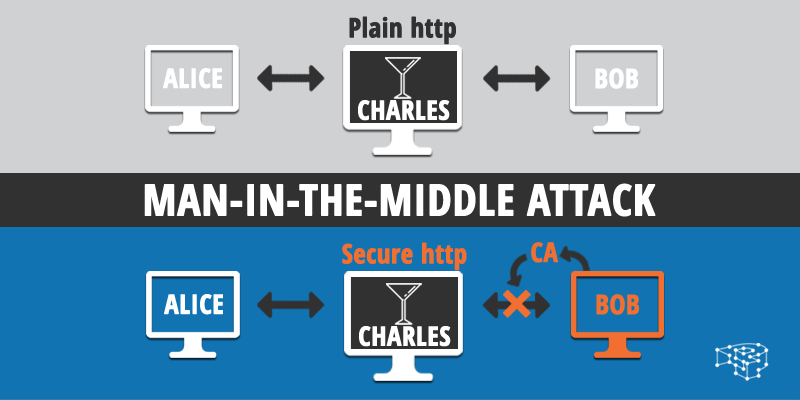
When Bob visits Alice’s website, he thinks he sends and receives data from Alice. In reality the data he sends passes through Charles, who in turn forwards them to Alice (making sure before doing that to either store them, or tamper them in some villainous manner). When Alice’s website responds, the data passes again from Charles to Bob. Its exactly like having a powerful wiretap. Aside from being able to store sensitive data such as emails, passwords and credit cards, Charles can even impersonate portions of Alice’s website, or Bob’s web browsing session.
So here we see where our two SSL allies, authenticated identity and secure communication come to the rescue!
When your website is protected by SSL, Man-in-the-middle attacks become much more difficult to pull off. When Bob connects to Alice’s website, he receives the server’s certificate and validates it against the CA. After the certificate is validated, the server and the client exchange some extra information and then data communication begins (such as what type of cipher they will use, a process called handshaking). If Charles would try to impersonate Alice by sending Bob his own public key, he wouldn’t go very far. Inside the certificate, there is a string of data called the digital signature, that ensures the file’s integrity. If any part of the certificate changes, the signature changes as well.
So if Charles attempted to change the public key, the CA would reject the certificate and notify Bob (because the digital signature calculated by the CA would not match the current one on the certificate). Since Charles does not have Alice’s private key, he can’t decrypt the communication. The only way for Charles to be able to do anything, is to try and compromise the CA’s servers as well.
But besides protecting you from martini-drinking bad guys, it also improves your SEO ranking! According to a Google Webmasters blog post by Zineb Ait Bahajji and Gary Illyes, HTTPS is used as ranking signal:
“We’ve seen positive results, so we’re starting to use HTTPS as a ranking signal. For now it’s only a very lightweight signal. But over time, we may decide to strengthen it, because we’d like to encourage all website owners to switch from HTTP to HTTPS to keep everyone safe on the web.“
Additionally as of September, the Google Security blog announced that the Chrome browser will begin explicitly labeling websites as “Not Secure”. This is done in an effort to “move towards a more secure web” and raise awareness in users.
How does it all work ?
So far we’ve talked about SSL certificates and how important they are in providing security and identity authentication. In this section we’ll roll up our sleeves and get into the nitty-gritty stuff!
SSL works by using a system called a public key infrastructure (or PKI, for sort).
PKI is a computer security system used to solve the problem of how to communicate securely over an insecure network. Simply put, if Alice and Bob want to communicate securely over the Internet, they need to exchange an encryption key of some sort. But if they do this, and someone who is in between them and owns a computer gets that key, he will be able to read all future communication! (it might not be a Charles type of person; system administrators due the nature of their work have access to all plaintext data passing through their servers too).
This might seem like a paradoxical problem, but it is solved through the use of not only one, but a pair of keys. A public, and a private one:
- Alice and Bob exchange their public keys. Since these are public, they can be sent over an insecure network with no worry. In fact, posting them in public is their intended use!
- Alice then encrypts the message she wants to send to Bob using her private key with Bob’s public key.
- Bob gets the message and decrypts it using his private key with Alice’s public key.
Private keys are usually stored locally on your computer (or USB drive, or somewhere where you know they are safe). No matter who reads your email, or network communication, they will only get a garbled-looking text without your private key.
Another useful aspect of public key encryption is the notion of the digital signature. We mentioned it earlier, when Charles would try and tamper with the certificate.
When Alice sends a message to Bob, she can also digitally sign it using her private key. This ensures that the message is indeed sent by Alice, and not by anyone else. The digital signature is in reality a long string of hexadecimal numbers that is calculated using the certificate’s information. Even if one byte changes in the certificate, the digital signature will change too, and the CA will reject it.
An SSL certificate is simply a data file that is installed on a system (typically on a web server) and works in the same manner. It encrypts communication, and ensures the identity of an entity (in our case, a website). It contains information such as:
- the certificate owner’s name
- email address
- duration of validity
- the fully qualified domain name of the web server
- the owner’s public key
- a digital signature that guarantees the certificate was not altered in any way.
It uses all this information to effectively associate an entity/organization with that system.
There are two ways to issue a certificate. The first is to sign it yourself (self-signed), while the second is to acquire it via a Certificate Authority (trusted).
What’s the difference between a self-signed and a trusted certificate?
A self-signed certificate provides the same level of encryption as a trusted one, but it does not guarantee the identity of the owner. It is mostly used for testing or in a local network infrastructure where there is no pressing need to have an owner tied to a system.
A trusted certificate on the other hand, provides both encryption and identity authentication. The certificate is issued by a third-party (CA) that verifies the identity of the certificate owner using a number of background checks.
So this means you need to trust the CA. What if it is a rogue one and how can one know?
This can certainly happen, and has happened in the past numerous times. Since this is indeed a matter of trust, the only solution is to make sure that the CA you are using is an known and established, respectable organization. CAs charge money for certification issuing (usually from as little as $10 to three-digit sums) but one should not fall into the trap of thinking that an expensive CA means more trust and safety!
How to SSL secure your website using Let’s Encrypt
There are many ways to generate a Let’s Encrypt certificate and install it on your web server. The process depends on whether you will be working from a Unix shell or not, what type of web server you are running, etc. Point your browser to Let’s Encrypt’s Getting Started page to find out more information.
If you’re an existing Pressidium client, things couldn’t be easier!
First, login to your Pressidium Portal account:
- Click on the SSL Certificates tab.
- Click on the Generate a free Let’s Encrypt certificate button.
- Select the website you want the certificate to be installed by choosing it from the Install Let’s Encrypt drop down menu.
- Finally, click on the Create & Install SSL Certificate button and you’re done!
In order to test whether the SSL is enabled on your website, open your browser and visit your website’s URL by using https in the address. If your browser displays the familiar green Secure padlock sign, you’re in business!
Your new Let’s Encrypt certificate has a 90-day time span but it will automatically re-new itself. You can also manage and install your own purchased certificates from the Portal. Read this Knowledge Base post to find all about it!
Security is a process, not a turn-key solution
The hard truth is that you can’t just buy something, or install a piece of software and forget about it, and think you have successfully dealt with all security issues. Computer security is a huge puzzle that involves technical mechanisms, policies, computers, and above all people and human psychology! You need to get all the pieces of the puzzle right and continuously tend to it. It is a process and not a turn-key solution.
The human factor is something that has been exploited again and again by malevolent users. We back up 100% any initiative that seeks to inform, provide tools and raise the public’s awareness of Internet security matters. In future posts we will delve into WordPress security aspects more deeply and thoroughly. WordPress is used by people and corporations to provide value and food on the table for many. Security incidents are not about website defacing and cyber-graffiti anymore but they tangibly affect the lives of others. And this is something that we take very seriously.
Start Your 14 Day Free Trial
Try our award winning WordPress Hosting!